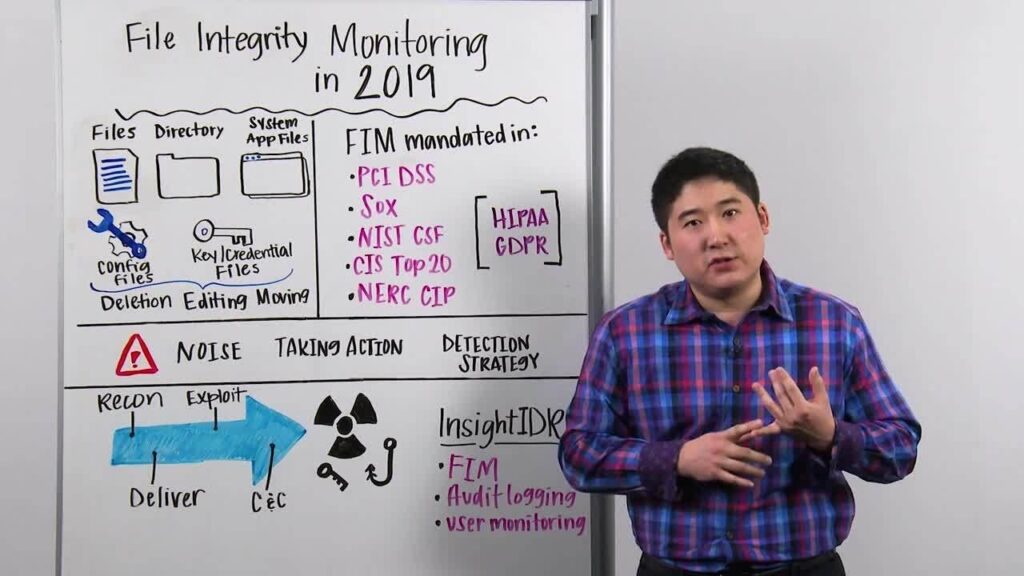
In the world of cyber security, there are many different terms and acronyms that can be confusing for those who are not in the know. One of these is FIM, which stands for File Integrity Monitoring. FIM is a process that helps to ensure the integrity of files by tracking changes and identifying unauthorized modifications.
This is important in order to protect data from being tampered with or stolen. FIM can be used to monitor both system and user files, as well as application code. When properly implemented, FIM can provide an early warning system against potential attacks on your systems and data.
In cyber security, Fim is an important tool that can be used to help protect against malicious attacks. Fim stands for file integrity monitoring and it is a way to monitor changes to files on a system. This can be used to detect malware or unauthorized changes that may have been made to files.
By monitoring the integrity of files, it is possible to help prevent data breaches and other security incidents.
Why File Integrity Monitoring is Important
File integrity monitoring is a process that helps ensure the data stored in files remains intact and has not been altered or corrupted. This is important because it helps to ensure the accuracy and completeness of the data, which is essential for businesses and organizations. File integrity monitoring can be used to detect unauthorized changes to files, as well as malicious or accidental changes.
It can also help identify errors that may have occurred during file transfers or storage.
What is File Integrity
File integrity is the security of a computer file or directory against unauthorized changes. These changes can be intentional, such as when a user edits a file, or unintentional, such as when a virus modifies a file. File integrity checking software can be used to detect these changes and alert the user.
There are several reasons why you might want to maintain file integrity. For example, you might want to make sure that sensitive data isn’t tampered with or that critical system files haven’t been modified by malware. Maintaining file integrity can also help ensure that software runs correctly and that backups are effective.
There are various ways to check for file integrity. One common method is to use cryptographic hashes, which create a unique fingerprint for each file. By comparing the current hash of a file with the original hash, you can tell if any changes have been made.
Other methods include checking file sizes and timestamps or using more sophisticated tools that monitor changes at the filesystem level.
Whichever method you choose, it’s important to regularly check forfile integrity and take action if any unauthorized changes are detected. By keeping an eye on your files, you can help keep your data safe from tampering or corruption.
File Integrity Monitoring Definition
What is File Integrity Monitoring?
File integrity monitoring (FIM) is the process of continuously tracking changes to files and directories on a computer or other electronic system. FIM can be used to detect unauthorized modifications to critical files, as well as malware that may have been introduced to a system.
How Does File Integrity Monitoring Work?
FIM works by comparing the current state of a file or directory against a known baseline. Any changes that are detected are flagged as potential problems that need to be investigated.
In some cases, such as when important system files have been modified, FIM can also trigger automated responses, such as reverting the changes or blocking access to the affected file.
Why Is File Integrity Monitoring Important?
FIM is an important part of security for any computer system.
By continuously monitoring files for changes, it’s possible to quickly detect and respond to potentially malicious activity. This can help prevent data breaches and other serious security incidents.
File Integrity Monitoring Best Practices
There is no single silver bullet when it comes to data security, but one of the best tools in the fight against data breaches is file integrity monitoring (FIM). FIM can help detect changes to critical files that could indicate an attempted or successful breach. When used properly, FIM can be a powerful tool for protecting your organization’s data.
Here are some best practices for using file integrity monitoring:
1. Define what constitutes a “critical” file. This will vary from organization to organization, but typically includes things like databases, web servers, and key application files.
Make sure you have a clear understanding of which files need to be monitored before you start setting up your FIM system.
2. Set up alerts for any changes to critical files. Once you know which files need to be monitored, you need to set up alerts so that you’re notified immediately if any changes are detected.
These alerts can be sent via email, text message, or other notification method.
3. Review logs regularly. It’s not enough to just set up alerts – you also need to regularly review the logs generated by your FIM system so that you can investigate any potential breaches.
Don’t wait until an alert is triggered – schedule time each week (or day) to review the logs and look for anything suspicious.
4. Keep your FIM system up-to-date .
File Integrity Monitoring Vendors
In order to maintain the integrity of your files, it is important to consider using a file integrity monitoring (FIM) vendor. FIM vendors offer tools that can help you detect and prevent changes to your files that could potentially lead to data loss or corruption. There are many different FIM vendors available, so it is important to do your research in order to find one that best suits your needs.
Here are some things to consider when choosing a FIM vendor:
What type of files do you need to monitor? Make sure the vendor offers support for the types of files you need to protect.
How often do you need to monitor for changes? Some vendors offer real-time monitoring while others only provide periodic scans. Choose a vendor based on how often you need file changes monitored.
What level of detail do you need? Some vendors only report on whether or not a change occurred, while others provide more detailed information about what was changed and who made the change. Choose a vendor based on the level of detail you require.
What other features does the vendor offer? Some vendors offer additional features such as alerts or reporting capabilities.
Credit: cybersecurity.att.com
What is Fim And Siem?
FIM and Siem are two types of enterprise software that help organizations manage their data. FIM stands for Financial Information Management and is a software application from Oracle that helps organizations manage their financial data. Siem stands for Service-Oriented Infrastructure Management and is a software application from IBM that helps organizations manage their infrastructure, including data center resources, networks and applications.
How Does a Fim Work?
How a FIM Works
A FIM, or Fuel Injection Motor, is a type of internal combustion engine that injects fuel directly into the cylinder. This direct injection of fuel allows for a more efficient burn of the fuel, which results in increased power and efficiency.
The FIM was first developed in the early 1900s, but did not gain widespread use until the 1970s.
The main advantage of a FIM over other types of engines is its higher efficiency. By injecting the fuel directly into the cylinder, there is less chance for it to be wasted through pre-ignition or incomplete combustion.
This also allows for a leaner air/fuel mixture to be used, which further increases efficiency. Additionally, the direct injection can help to cool the intake charge, which can lead to even more power gains.
One potential downside of a FIM is that it can be more difficult to start in cold weather than other types of engines.
This is because the fuel needs to be vaporized before it can be injected into the cylinder, and this can be difficult to do in cold temperatures. However, once the engine is started and warmed up, it should run just as well as any other type of engine.
Overall, a FIM provides many advantages in terms of power and efficiency gains over other types of engines.
If you are looking for an upgrade for your vehicle, consider switching to a FIM!
What is Fim Information Technology?
FIM information technology, or FIM IT, is a type of software that helps organizations manage and automate their business processes. It can be used to track and monitor data, create and maintain records, generate reports, and more. FIM IT is often used in conjunction with other software applications, such as enterprise resource planning (ERP) and customer relationship management (CRM) systems.
FIM IT is typically deployed on-premises, but there are also cloud-based solutions available. On-premises deployment requires organizations to purchase the software and install it on their own servers. Cloud-based solutions are offered as a service by providers such as Microsoft Azure and Amazon Web Services.
Organizations can pay for these services on a subscription basis, which can be more cost-effective than purchasing on-premises software.
When choosing a FIM IT solution, organizations should consider their needs and budget. They should also make sure that the solution is compatible with their existing systems and will meet their future needs.
What are Fim Requirements?
FIM requirements are the guidelines that must be met in order to be certified under the FIM racing sanction. There are four main areas of focus: safety, technical, administrative and financial.
The safety requirements are in place to ensure that all riders are protected from potential harm during a race.
All riders must wear approved helmets and protective clothing, and bikes must be equipped with certain safety features such as working brakes and handlebar padding. The track itself must also meet certain safety standards, including being free of obstacles and having adequate barriers in place.
The technical requirements relate to the bike itself.
There are strict rules about what modifications can be made to the bike, and it must pass a pre-race inspection by a qualified mechanic. The bike must also meet certain size and weight limits.
The administrative requirements cover things like rider registration and licensing, as well as team membership rules.
Riders must also have medical insurance in case of injury during a race.
Finally, the financial requirements stipulate how much money teams and riders need to raise in order to participate in FIM-sanctioned events. These funds go towards paying for things like race entry fees, travel expenses and mechanical support.
What is INTEGRITY in Cyber Security (CIA Triad!) | LIVE DEMO (FIM/File Integrity Monitor)
Conclusion
Fim stands for File Integrity Monitoring. It is a process of continuously monitoring and verifying the integrity of files to detect any unauthorized changes that could potentially jeopardize the security of the system. Fim can help prevent data breaches and ensure compliance with regulatory requirements.